The destination server is unavailable continent tls client. TLS and SSL: Minimum knowledge required
The Continent TLS program helps users gain secure access to certain web resources. Key information is stored in a secure container.
Usage
Users of the corporate network can now get remote and secure access to specific resources on the Internet. During connection establishment, mutual authentication with the server is provided. To gain access, you must enter the site address in your browser. As a result, the client processes and sends the request to the server to create a secure connection. Authentication is provided based on key certificates.
Client capabilities
The connection protocol between the server and the Client is TLSv1. The resource for which a secure contact is established must contain the TLS value in the server name. If everything is done correctly, the display will display a certificate that can be updated by pressing the appropriate button. It is possible to automatically remember your login and password when logging into the system. It is worth noting that if you enter false information 5 times in a row during the authorization process, the system will automatically be blocked. You can re-enter the data only after 10 minutes.
Key Features
- the program is fully compatible with all versions of Windows;
- during use, reliable protection is provided between corporate users;
- such a Client is the optimal solution when data is exchanged and information leakage is unacceptable;
- To log in you will need to enter your data (login and password) and run a certified key;
- work is carried out only with servers that support TLSv1 and TLSv1.2 protocols.
To install the Continent TLS Client software you need:
Figure 33. Start window of the “Continent TLS Client” software installation wizard.

Figure 34. License agreement window for the Continent TLS Client software.
3. Check the “I accept the terms of the license agreement” box and click the “Next” button. A window will appear on the screen for entering the license key supplied with the Continent TLS Client software on paper or electronic media.

Figure 35. Window for entering the license key of the Continent TLS Client software.
4. Enter the license key and click Next. A dialog for selecting the installation path for the Continent TLS Client software will appear on the screen.

Figure 36. Window for selecting the installation path for the Continent TLS Client software.
5. Leave the default installation path. Click "Next". The “Launch Configurator” dialog will appear on the screen.

Figure 37. Launch window for the Continent TLS Client software configurator.
6. Check the “Run the configurator after installation is complete” checkbox.

Figure 38. Readiness window for installing the Continent TLS Client software.
8. Click the "Install" button. The installation of the component will begin.

Figure 39. Installation process of the Continent TLS Client software.
9. The “Continent TLS Client” software settings dialog will be displayed on the screen.

Figure 40. Configuring the Continent TLS Client software.
To configure the software you need:
a) In the “Continent TLS Client Settings” section, leave the “Port” value at its default value of 8080.
b) In the “Protected server settings” section, in the “Address” field, set the TLS server name: lk.budget.gov.ru.
c) In the “Protected server settings” section, in the “Certificate” field, specify the TLS server certificate file copied to the local directory in clause 3.1 of this Guide.

Figure 41. Configuring the Continent TLS Client software. Selecting a certificate.
d) If the user’s workstation does not use an external proxy server, click the “OK” button.
e) Otherwise, indicate the address and port of the organization's external proxy server used.

Figure 42. Configuring the Continent TLS Client software service. Setting up an external proxy server.
f) Click the “OK” button.
10. A dialog for completing the installation of the Continent TLS Client software will be displayed on the screen.

Figure 43. Dialogue for completing the installation of the Continent TLS Client software.
11. Click the “Done” button.
12. A dialogue will appear on the screen about the need to reboot the user’s workstation.

Figure 44. Dialogue about the need to reboot the User's workstation.
13. Click the “No” button.
Software Continent TLS VPN– a system for providing secure remote access to web applications using GOST encryption algorithms. Continent TLS VPN provides cryptographic protection of HTTP traffic at the session level. Information is encrypted using the GOST 28147–89 algorithm.
Identification and authentication of remote users
Identification and authentication of users are performed using public key certificates of the x.509v3 standard (GOST R 31.11–94, 34.10–2001). Continent TLS VPN checks key certificates against certificate revocation lists (CRLs). Certificates are issued by an external certification authority.
If the authentication procedures are successfully completed, the user's request is redirected via HTTP to a secure network to the appropriate web server. In this case, special identifiers (client identifier and IP identifier) are added to each user's HTTP session.
Cryptographic protection of transmitted information
Continent TLS VPN provides cryptographic protection of HTTP traffic at the session level. Information is encrypted using the GOST 28147–89 algorithm. The hash function is calculated using the algorithm GOST R 34.11–94, GOST R 34.11–2012. The generation and verification of an electronic signature is carried out in accordance with the algorithm GOST R 34.10–2001, GOST R 34.10–2012.
Hiding protected servers and address translation
Continent TLS VPN filters requests and transmits request addresses to web servers on the corporate network. Address translation is carried out in accordance with the rules set by the “Continent TLS VPN” administrator.
Fault tolerance and scalability
Continent TLS VPN supports operation in a high-performance cluster design with load balancing (external load balancer). Increased fault tolerance is achieved by adding a redundant node to the cluster. At the same time, the expansion of balancing cluster elements can be carried out unlimitedly. Failure of a cluster element does not lead to broken connections, since the load is evenly distributed among the remaining elements.
Event Monitoring and Logging
In Continent TLS VPN, the administrator can always obtain operational information about the current state of established connections and statistics on its operation. Information security events are logged on the server. All events can be sent to a specified server in syslog format for further analysis, which makes integration with SIEM systems as simple as possible.
Convenient management tools
The combination of local and remote tools with a web interface and a convenient graphical management console provides flexible configuration of Continent TLS VPN in accordance with the requirements of security policies.
Supported protocols
Continent TLS VPN supports TLS v.1, TLS v.2 protocols.
User experience via any web browser
Using the Continent TLS VPN Client application, users can access protected resources from any web browser. Continent TLS VPN Client is a local proxy, intercepts browser traffic to protected web servers and packs it into an http tunnel. Thanks to this, the user can work with any web browser installed on his device.
Using a user-friendly software client
Using a user-friendly software client Continent TLS VPN Client or CryptoPro CSP version 3.6.1 can be used as a client on the user’s device.
Continent TLS VPN- a certified solution for protecting remote users’ access to protected resources.
Continent TLS VPN has a client-server architecture and consists of the CIPF “Continent TLS VPN Server”, which is installed at the edge of the network perimeter, and the VPN client of the CIPF “Continent TLS VPN Client”, installed on the computers of remote users. “Continent TLS VPN Server” ensures confidentiality, integrity and imitational protection of transmitted information and performs the following functions:
- user authentication using public key certificates of the x.509v3 standard (GOST R 31.11–94, 34.10–2001);
- checking the user certificate against the CRL revocation list;
- establishing secure encrypted connections using the HTTPS protocol;
- broadcasting requests to corporate network web servers and others.
Continent TLS VPN Server IPC-3000F (S021), 2014
CIPF “Continent TLS VPN Client” is a local transparent proxy service that provides mutual authentication with the server, establishment of a secure connection, and exchange of encrypted data with the server. It is also compatible with most existing internet browsers. In addition, it is possible for users to work through the “Continent TLS VPN Server” without installing the CIPF client software “Continent TLS VPN Client”. In this case, the user’s computer must use the MS Internet Explorer browser with the installed cryptoservice provider “CryptoPro CSP” (version 3.6 or 3.9), which provides support for GOST cryptoalgorithms.
The product is intended for:
- securely connect users to government service portals, electronic trading platforms, Internet banking systems or corporate applications via a web browser.
- cryptographic protection of http traffic when transmitting data over open channels of public networks.
Key Features
- Cryptographic protection
- The use of the TLS protocol with encryption in accordance with GOST 28147–89 ensures reliable protection of HTTP traffic at the transport level
- Monitoring and logging information security events
- Obtaining operational information about the operation statistics and current connections of the “Continent TLS VPN” server
- User Identification and Authentication
- Identification and authentication of users using public key certificates of the x.509 standard. Transmitting user authentication data to the web server.
- Working with external certification authorities (CA)
- To create x.509 certificates, “Continent TLS VPN” uses the external CA “CryptoPro”
- Transparent proxying of HTTP traffic
- To securely log into the web service, the user just needs to enter the IP address or domain name in the address bar of the browser.
- Scalability and fault tolerance
- Support for operating mode in a high-performance cluster scheme with load balancing (external load balancer). Increased fault tolerance is achieved by adding a redundant node to the cluster.
Peculiarities
- High performance – up to 20,000 simultaneous connections per node (IPC-3000F).
- Compatible with any web browsers.
- Ease of management – all settings are carried out by the administrator via a web browser.
- Unlimited performance scalability - the ability to combine into a high-performance cluster to achieve performance of over 100 thousand simultaneous connections.
- Ease of implementation and operation - a ready-made solution eliminates the need to embed cryptographic modules into the web server and go through the procedure for monitoring the integration of cryptographic information protection.
- Easy integration with external SIEM systems.
Certificates
- Certificate of FSTEC of Russia for compliance with the requirements for the absence of non-compliance with the 4th level of control. It is used to protect AC up to class 1G inclusive, ISPDn up to UZ 1 inclusive and GIS up to class 1 inclusive.
- Certificates of the FSB of Russia “Continent TLS VPN Server” for CIPF class KS2 and “Continent TLS VPN Client” for CIPF class KS2 and KS1.
2018: Release of "Continent TLS Server" version 2.1

Customers of Continent TLS Server 2.1 were able to centrally update the client part of the complex on the computers of remote users. In addition, in the presented version the product licensing system was simplified: for a cluster of several devices, only one license is required for the maximum number of simultaneous connections. It was also decided to combine licenses for connecting to a proxy server and licenses for connecting via a TLS tunnel. All this simplifies operation and selection of the appropriate solution architecture.
As of July 2018, “Continent TLS Server” 2.1 was submitted for certification to the FSB of Russia. After passing the tests, the product will be certified according to classes KS1 and KS2.
| This version of the Continent TLS Server product is designed to facilitate the work of administrators during the period of change in encryption standards and provide the ability for convenient monitoring. Changes in licensing policy and the ability to allocate a separate product management port should expand the scope of its application. Support for a wide range of TLS clients will allow you to quickly build a system of secure access to a web application where third-party crypto providers are already used. Now our product supports "CryptoPro", "Validata" and the trusted browser "Sputnik". |
2016
High dynamics were also demonstrated by the relatively new (released in 2015) products of the “Continent” line – “Continent TLS VPN” and the “Continent” crypto switch. Their sales volume amounted to 71 million rubles. and 62 million rubles. respectively. The demand for “Continent TLS VPN” was due to the growing interest of customers in the use of Russian encryption algorithms to protect access to government portals, as well as in organizing secure remote access using GOST algorithms. A factor in the growth of sales of Continent crypto switches was the need to protect communication channels in geographically distributed data centers.
The technical release “Continent TLS VPN” 1.0.9 has been released with an application portal
The Security Code company announced in April 2016 the release of a technical release of the product version “Continent TLS VPN”, designed to provide secure remote access to information systems that process personal data (ISPD) and government information systems (GIS). The product has a number of new features.
One of the most significant changes in "Continent TLS VPN" 1.0.9 is the creation of an application portal with the ability to authenticate and authorize using credentials from Active Directory. This improvement significantly simplifies the process of managing access to corporate web services for various categories of users. For example, using a portal you can provide a single point of access for company employees and its contractors. In this case, the set of available applications will depend on the category and user rights.
Another difference is the addition of the ability to create a server start page, accessible via the open HTTP protocol. It allows you to significantly reduce the cost of maintaining a secure web application.
Version 1.0.9 also adds the ability to operate the product in TLS tunnel mode, which allows the remote user to remove restrictions on interaction through a channel encrypted using the TLS protocol. Such a connection allows you to provide access not only to web resources, but also to other types of applications, for example, terminal servers (via the RDP protocol) or “thick clients” for corporate applications (ERP, CRM, etc.). This approach significantly increases the number of remote access scenarios in which Continent TLS VPN can be used.
“Security Code” assessed the timing of the transition of government agencies to Russian encryption tools
On July 16, 2016, the President’s order to the head of government was published on the Kremlin website on the need to prepare the transition of government bodies to the use of Russian cryptographic algorithms and encryption tools by December 1, 2017. In particular, the government must ensure the development and implementation of a set of measures necessary for a phased transition to the use of Russian cryptographic algorithms and encryption tools, as well as provide free access for citizens of the Russian Federation to the use of Russian encryption tools.
The published document will entail certain steps to bring the IT infrastructures of government agencies into compliance with the stated requirements. In particular, mass installations of domestic cryptographic information protection tools (CIPF) in addition to existing solutions are expected in government agencies.
More details:
- Yarovaya Law (On amendments to the Criminal Code and the Code of Criminal Procedure of the Russian Federation regarding the establishment of additional measures to counter terrorism)
Security Code experts note that the innovation will primarily affect government service portals of federal and regional departments. At the same time, the implementation of this task affects two aspects: the implementation of CIPF on the web server side and on the user side. If we assume that the users will embed a certified crypto library into the browser, then the problem can be solved on the web server side in two ways.
One of them is the integration of CIPF into web servers, the second is the implementation of a software and hardware complex (SHC) with the implementation of TLS VPN (one of such products is the “Continent TLS VPN Server”, developed by the “Security Code”), which will intercept HTTP /HTTPS traffic and encrypt it in accordance with the encryption algorithm according to GOST (28147-89). Each of the options has its own characteristics - both from the point of view of technical implementation and from the point of view of the timing of the project.

According to Security Code analysts, in the first case (embedding), the stages of work will be as follows:
- Development of organizational and administrative documentation (ORD) - 2 months;
- Implementation - 0.5 months;
- Monitoring the integration of CIPF into the FSB of Russia - 7 months;
As a result, such a project can be completed within 1 year.
When choosing the PAC installation option, the project will be divided into the following stages:
- Development of operational documentation - 2 months;
- Conducting an open competition under 44-FZ - 2.5 months;
- Supply of equipment and software - 1.5 months;
- Implementation - 0.5 months.
The total duration of the project in this case will be about 7 months.
Security Code experts note that, based on generally accepted practice, at least three months pass between the issuance of instructions to the government and the start of work by companies on projects (taking into account the need to develop and adopt by-laws). Accordingly, there is a risk that organizations that choose the option of embedding CIPF into web servers will have difficulty meeting the deadlines set by the president. And if the adoption of by-laws is delayed for more than three months, implementation deadlines may be missed.
“In addition to difficulties with timing, the first path - embedding - is associated with other difficulties. These are additional labor costs, first for preparing and approving a package of documents for the testing laboratory, and then for making changes to the code and debugging the application based on the results of the analysis of the testing laboratory. But the main advantage of the second option is that when choosing a PAK, the customer receives a powerful, high-performance industrial solution designed for large organizations. It is scalable, easy to manage, compatible with any Internet browsers, and easily integrates with external SIEM systems,” said Pavel Korostelev, product marketing manager at Code Security.
Taking into account the above, the “Security Code” recommends that government customers choose the optimal algorithm for complying with legal requirements and follow the path of implementing a software and hardware system (SHC) with the implementation of TLS VPN. For secure access of remote users to web resources, the software and hardware complex “Continent TLS VPN” certified by the FSB of Russia is used. It is easy to deploy, has a free TLS client for end users, and can support over 100K simultaneous connections.
Russia dated July 30, 2015 SF/124–2676 on the CIPF “Continent TLS VPN Server” and SF/525-2677, SF/525-2678 on the CIPF “Continent TLS VPN Client” (version 1 and 2) confirm compliance with the requirements of the FSB Russia to encryption (cryptographic) means of class KS2 and KS1. Certificates of the FSB of Russia authorize the use of CIPF “Continent TLS VPN” for cryptographic protection of information that does not contain information constituting a state secret.
FSTEC Certificate of Russia No. 3286, issued on December 2, 2014 for the CIPF “Continent TLS VPN Server”, confirms the product’s compliance with the requirements of the guidelines for the 4th level of control for the absence of non-compliance with non-compliance and allows its use when creating systems up to security class 1G inclusive and for information protection in ISPDn and GIS up to 1st grade inclusive.
Setting up an automated workplace of the Electronic Budget occurs in several stages; they are not complicated, but require care. We do everything according to the instructions for setting up an electronic budget. Short and to the point...
Electronic budget setting up a workplace
Root certificate electronic budget
Create a key folder in My Documents to store downloaded certificates in this folder:
On the website http://roskazna.ru/gis/udostoveryayushhij-centr/kornevye-sertifikaty/ in the GIS menu -> Certification Authority -> Root certificates, you need to download “ Root certificate (qualified)" (see figure), or if you received a flash drive with certificates, copy them from the Certificates folder.
Certificate Continent TLS VPN
The second certificate that needs to be downloaded is the Continent TLS VPN certificate, but I couldn’t find it on the new roskazna website, so I’m putting a link from my website. Download the Continent TLS VPN certificate to the key folder; we will need it later when we configure the Continent TLS client program.
Install the downloaded Root certificate (qualified) for working with the electronic budget.
In the START menu -> All programs -> CRYPTO-PRO -> launch the Certificates program.
Go to Certificates as shown in the figure below:

Go to the menu Action - All tasks - Import, the Certificate Import Wizard window will appear - Next - Review - Find the downloaded Root certificate (qualified) in our case it is located in My Documents in the key folder

If everything was done correctly, the root certificate of the Federal Treasury CA will appear in the certificates folder.

Installation of "Continent TLS Client" for working with electronic budget
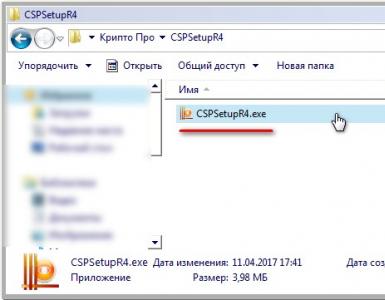
Continent_tls_client_1.0.920.0 can be found on the Internet.
Unpack the downloaded archive, go to the CD folder and run ContinentTLSSetup.exe

From the item, click on Continent TLS Client KC2 and start the installation.


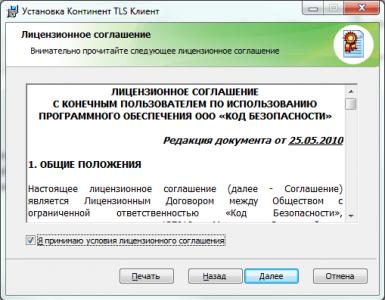
We accept the terms

Leave the destination folder as default

In the configurator launch window, check the box next to Launch configurator after installation is complete.
During installation, the Service Settings window will appear:

Address - indicate lk.budget.gov.ru
Certificate - select the second certificate downloaded earlier in the key folder.

Click OK and complete the installation, Done.

When asked to reboot the operating system, we answer No.
Installing the electronic signature tool “Jinn-Client”
You can download the Jinn-Client program on the Internet.
Go to the Jinn-client - CD folder, run setup.exe

Click from the Jinn-Client list, the program installation starts

We ignore the error, click Continue, Next, accept the agreement and click Next.

Enter the issued license key

Install the program as default, click Next


We complete the installation, answer the question about rebooting the operating system No
Installing a module for working with electronic signatures “Cubesign”
If you need an archive with the program, write in the comments.
Run the installation file cubesign.msi


Setting up the Mozilla Firefox browser to work with the Electronic Budget.
1. Open the "Tools" menu and select "Settings".
2. Go to the “Advanced” section to the “Network” tab
3. In the “Connection” settings section, click the “Configure…” button.
4. In the connection parameters window that opens, set the value
"Manually setting up a proxy service."
5. Set the values of the HTTP proxy fields: 127.0.0.1; Port: 8080.

6. Click the “OK” button.
7. In the “Settings” window, click the “Ok” button.
Login to your personal account of the Electronic Budget
A window will open asking you to select a certificate for logging into your Electronic Budget personal account.

We select a certificate to enter the Personal Account of the Electronic Budget, if there is a password for the closed part of the certificate, write it down and click OK, then the Personal Account of the Electronic Budget will open.